☰
CRETAN SECURITY OPERATIONS CENTER

CRETAN SECURITY OPERATIONS CENTER

As summer rolls around, many of us look forward to a break—whether it's a quiet weekend, an extended vacation, or a national holiday. But if there’s one group that doesn’t seem to take time off, it’s cybercriminals.
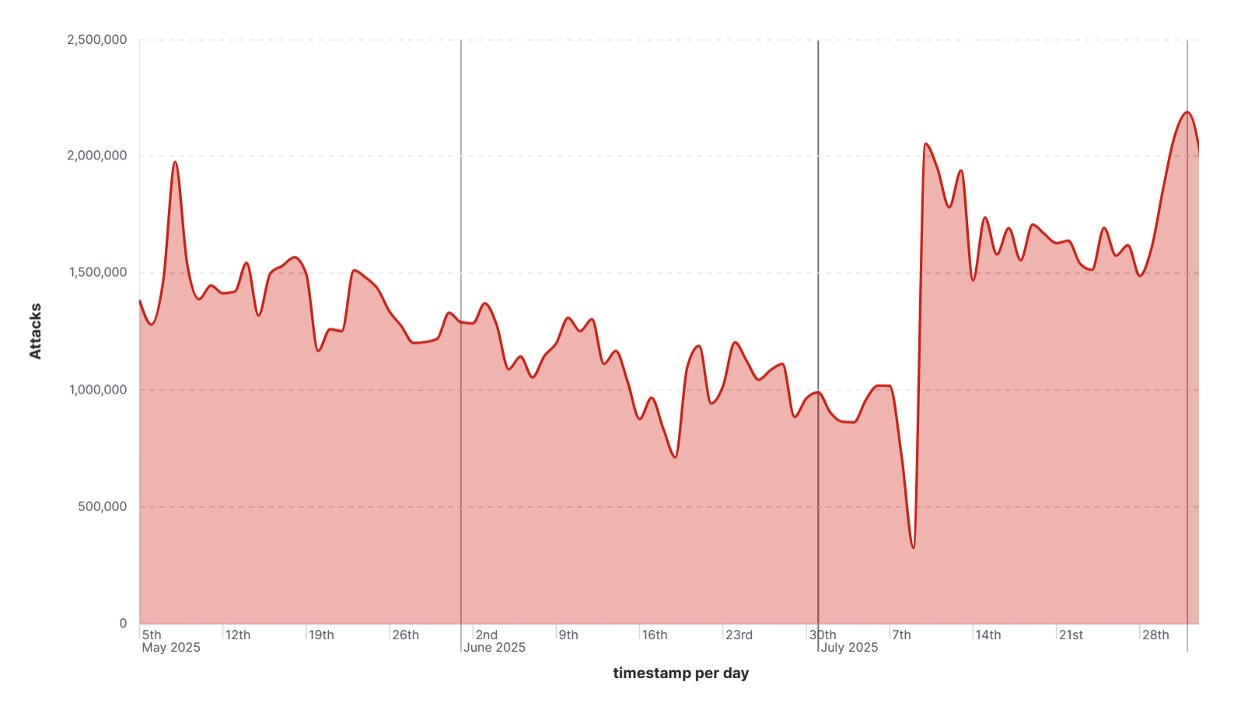
Our recent analysis of honeypot data from the Cowrie system reveals an unsettling truth: cyberattacks remain consistent—and even spike—during the holiday months of May, June, and July.
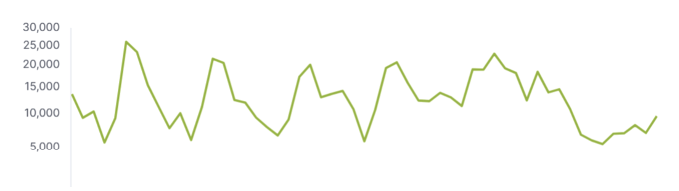
The chart above shows attack activity against our C-SOC systems from May through July 2025. The line (representing the number of attacks per day) tells a clear story:
Why Don’t Attacks Stop for the Summer?
Summer might be a time for rest and relaxation, but cybercriminals don’t share the same calendar. The data shows that threat actors remain active during the months when defenders are likely to be understaffed. As we head into future holiday seasons, let’s make sure our cybersecurity posture stays sharp.

We recently ran a set of honeypots to observe how attackers behave in the wild. The results? Alarming, but not surprising.
This word cloud represents the most commonly attempted passwords used by attackers trying to access our systems. It’s a visual map of laziness — not on the part of the attackers, but of the systems and users they expect to find. “admin”, “123456”, “password”, “qwerty”, and even (empty) were among the most frequent. Some tried to get clever with variants like “P@ssword123” but the pattern is clear: attackers are relying on the fact that many systems still go live with default or weak credentials.
What’s striking is how automated and consistent these attempts are. Attackers don’t waste time brute-forcing passwords like in the movies — they spray the internet with credential stuffing attacks based on known weak patterns, default setups, and past breaches. And far too often, it works.
This data should serve as a wake-up call. Weak passwords are not just a user issue — they’re a systemic risk, especially when default configurations are pushed into production without proper hardening. We need to do better across the board.
If you're responsible for infrastructure, audit your exposed services. If you're managing users, enforce strong password policies and MFA.
Cybersecurity doesn’t start with zero-day exploits. It starts with not leaving the front door wide open.
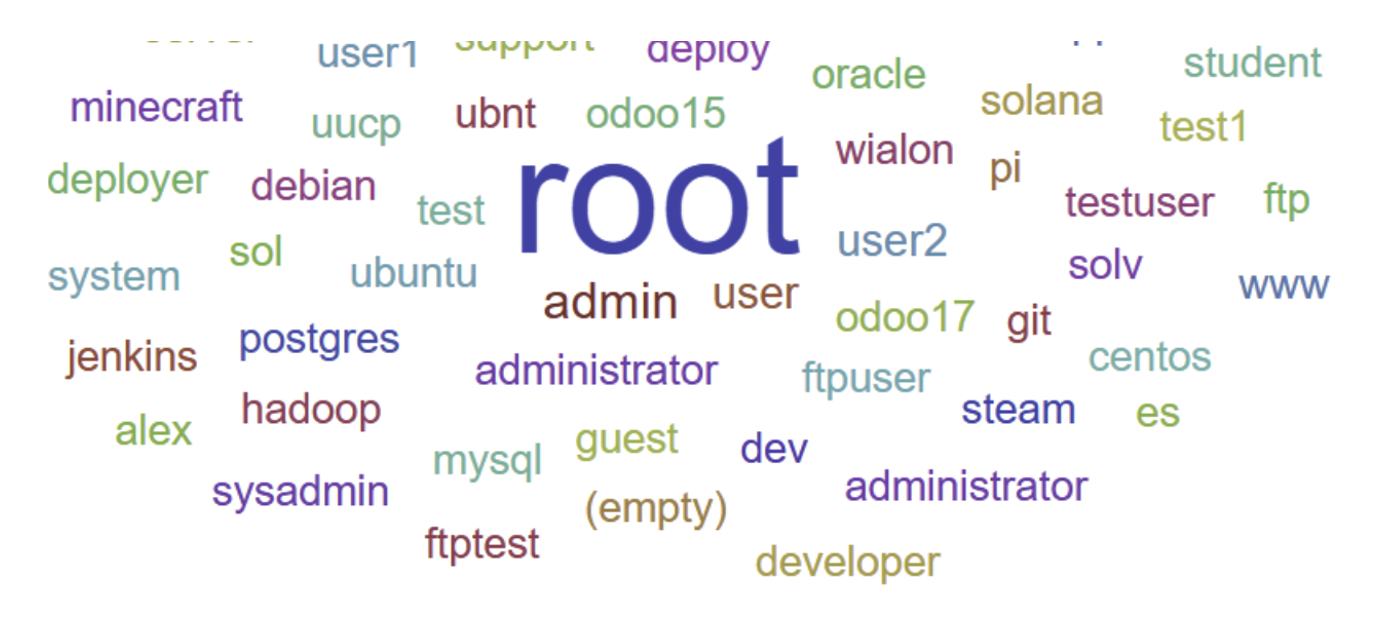
Every second, attackers are scanning, probing, and striking. Our honeypots recently recorded an intense wave of unauthorized login attempts — not just a few dozen, but hundreds of thousands. The image above shows the most commonly used usernames in those attacks. And behind each one is something deeply serious: a cybercriminal actively trying to break into systems like yours.
These Aren’t Random Attacks — They’re Deliberate and Dangerous
What we’re seeing is targeted aggression at scale. The most frequently tried usernames include:
These aren’t accidents. They’re signs of well-crafted attack scripts that cycle through known default accounts, forgotten services, and high-value entry points — hoping for just one hit.
These login attempts came from thousands of unique IPs spread across the globe, likely part of massive botnets. Their behavior is consistent, persistent, and dangerous:
This is not noise. This is hostile reconnaissance followed by action. And once they’re in, they move fast.
The Cost of ComplacencyOne missed alert, one forgotten test account with a weak password, one exposed SSH port — that’s all it takes. And once attackers gain a foothold, they don’t just sit idle. They:
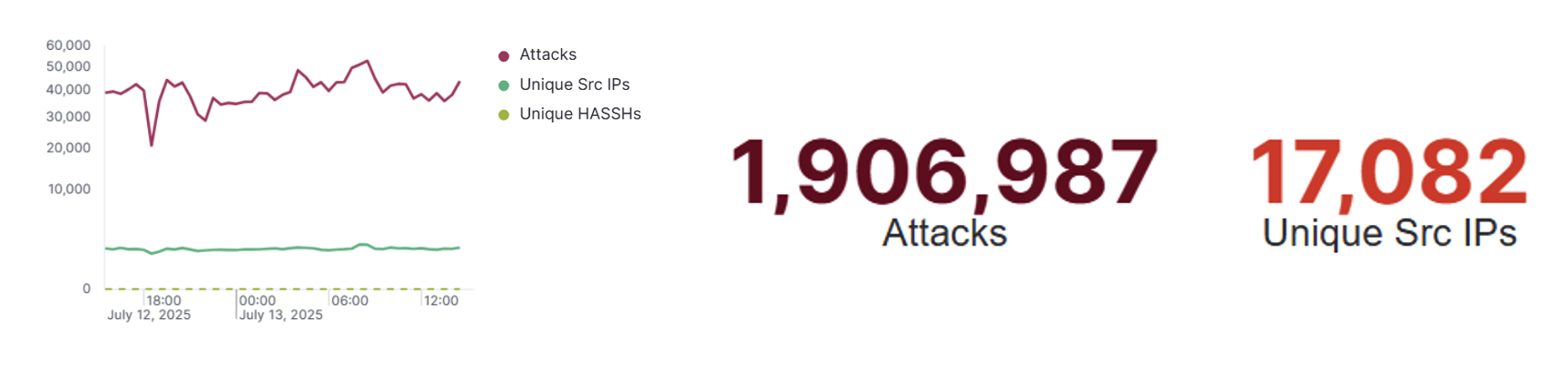
In today's hyper-connected world, monitoring and mitigating cyber threats requires not just intelligence, but visibility. One powerful example of this in action is the Cretan Security Operations Center’s (C-SOC) dashboard.
Our dashboard shows a staggering of 1.9 million recorded attacks, with over 17,000 unique source IPs. This highlights not just the scale of global cyberattacks, but the diverse sources they're originating from.
Forget the Hollywood image of lone hackers in dark rooms. Today’s attacks are often automated, persistent, and globally distributed. Whether driven by botnets, nation-state actors, or criminal syndicates, these attacks target:
It’s not just about stealing data anymore — it's about disruption, surveillance, extortion, and control. Our dashboard highlights over 17,000 unique source Ips per day. This isn’t random — it’s orchestrated. These IPs often belong to:
The scale and speed of these operations make traditional defenses obsolete. We’re in the era of machine-speed attacks, where detection and response must also be automated and intelligent. These numbers aren’t just statistics. Each attack attempt represents a threat actor probing our digital walls, looking for a way in. Multiply that by 1.9 million — and the message is clear:
Our honeypots are under constant siege—day and night, they are relentlessly targeted by malicious actors from all corners of the internet. On average, we observe over 1,000 distinct attackers every hour. This steady stream of intrusion attempts isn't just a reflection of automated scans or idle curiosity; it's a coordinated, systematic effort to gain control over our systems.
But this raises an important question: What exactly are these attackers looking for? What value do they see in our systems that drives this persistent activity? To answer that, we need to go beyond just counting login attempts—we need to examine what happens after an attacker believes they’ve successfully infiltrated a system.
One of the first things many attackers do post-login is run system reconnaissance commands. A commonly observed command is cat /proc/cpuinfo. This tells the attacker crucial information about the machine’s CPU—what kind of processor it uses, how many cores it has, and other architecture details. In other words, they want to understand the raw computational power at their disposal.
Another frequently executed command is free -m | grep Mem, which reveals how much memory is available on the machine. Memory capacity, along with CPU strength, helps attackers determine how suitable the system is for various malicious tasks.
This kind of system profiling is not random. It’s a calculated step to evaluate what kind of malware would be most effective on the compromised host. If the system has a powerful CPU and sufficient RAM, it might be an ideal candidate for cryptocurrency mining. If the attacker is looking for network throughput and uptime, the system might instead be repurposed as a SPAM relay server, a phishing host, or even a platform to launch further attacks.
Ultimately, this reconnaissance phase gives us valuable insight into the attacker’s intent. By analyzing their behavior—not just their presence—we can better understand their goals and motives. And this, in turn, helps us to not only design stronger defenses, but also anticipate the kinds of abuse a compromised system might be subjected to.
Our honeypots are being hammered with attacks both day and night. We get roughly 150,000 attacks every three hours. This is how the attacks look like for a period of one week:
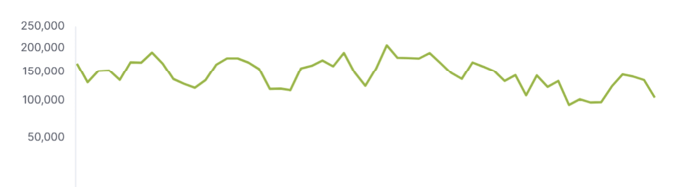
Although there are some peaks and troughs, the intensity of attacks ranges does not fall below 100,000 attacks every three-hour interval – which is about half of the maximum intensity we see of roughly 200,000 attacks every three hours. Focusing on attacks coming from a single country shows something like a diurnal cycle with a noticeable difference between peaks and troughs:
But, when averaging over all countries, the differences collapse. So, do attackers sleep at night? We do not really know, but we do know that attacks continue with ferocious intensity both day and night.
C-SOC has been operating a honeypot infrastructure that is being used to study attackers and their attack patterns. It is impressive to see the volume of attacks we receive. On the average we receive more than 55,000 attacks per hour coming from 1,300 (unique) IP addresses. The attackers want to log in our systems trying various usernames and passwords. The most common username tried was “root” and the most common password “123456”. Although these obvious passwords can be easily caught, attackers use non-obvious combinations of user names and passwords, most probably taken from past password leaks of vulnerable web sites.